LinkedIn the Middle
Last week, LinkedIn announced a major new service called Intro. In response, the Internet community spontaneously burst into flames:
LinkedIn has a new iOS app called Intro. Here’s why you should treat it like a radioactive wasp hive. bishopfox.com/linkedin-intro/
— Eric A. Meyer (@meyerweb) October 25, 2013
On the surface, Intro is rather clever. It dips into LinkedIn’s trove of professional profiles and inserts miniature bios at the top of inbound emails. Intro’s bios are interactive, making it a snap to learn how a sender’s professional network overlaps with your own:
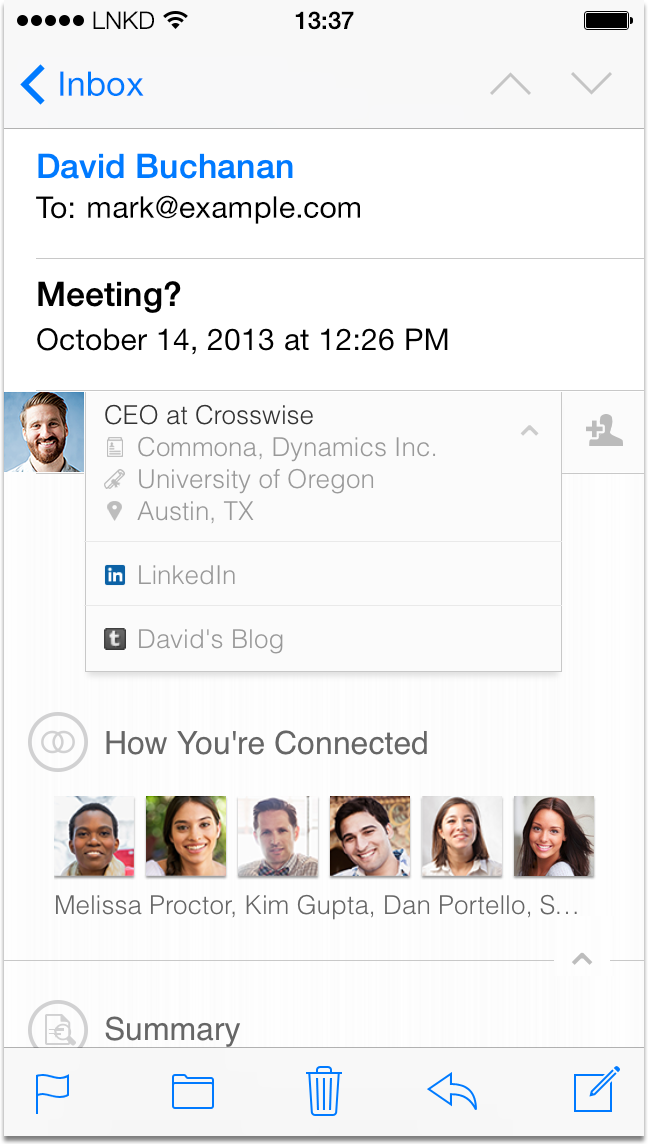
Intro is a great feature. Its implementation, on the other hand, has made Mr. Internet quite cranky. Apple’s Mail app can’t be extended by third parties. LinkedIn flanks this problem by extending emails instead. To do so, Intro inserts itself between you and your email provider, rewriting your emails before they reach your inbox. Depending on one’s perspective, this approach is either clever or crazy. In the crazy column, it grants LinkedIn full and unencrypted access to your most personal communications. In the world of online security, such men-in-the-middle are bright red flags. They’re potential points of weakness and tempting targets for attack. Adding middlemen to the mix is usually the wrong way to go; the benefits must measurably outweigh the costs.
There are other concerns. Historically, LinkedIn has a poor track record managing security-critical infrastructure. In addition, Intro opens up new avenues for phishing and other mayhem. Finally, using Intro means your email is only available when both LinkedIn and your underlying mail provider are up and running.
Configuration Profiles
Many developers have also sounded the alarm about Intro’s use of configuration profiles to alter iPhone mail settings. It’s worth teasing this apart a bit, since even in the iOS community there appears to be some confusion1.
Introduced with iOS 4 and Apple’s push into the mobile enterprise, configuration profiles are signed bags of system-wide settings. They can contain all sorts of useful (or troubling) settings, ranging from VPN configurations, to email accounts, to root certificates. It’s possible to directly inspect the contents of profiles before installing them2 but, for most users, the inspection dialog might as well be Greek.
There are three direct ways to install configuration profiles: via the web, via email attachments, or via connection to a PC. Native apps cannot directly install profiles, although they can direct users to profile download pages in Mobile Safari. This mostly leaves profile installation outside of Apple’s review and control. (As it happens, LinkedIn Intro is a web, not native, app, and is thus entirely outside Apple’s purview.)
There’s also an indirect way to install configuration profiles called Over-The-Air Profile Delivery. OTA delivery is typically used by larger companies whose employees wish to bring their own devices to work. Devices must first be enrolled in a management service. Enrollment is achieved via a complex multi-step process, with plenty of obtuse warning dialogs proffered by iOS along the way. Once enrolled, devices can recieve arbitrary settings updates from their management services at any time.
It’s worth stating that LinkedIn Intro does not use mobile device management
(MDM) profiles3; it does not use OTA
delivery. As a result, it cannot push arbitrary changes to your device at any
time. The confusion in the iOS community may stem from the fact that, when
installed, Intro does issue a device enrollment challenge. Typically, device
enrollment challenges are the first step in the larger MDM enrollment dance.
However, Intro installation stops short of fully enrolling the device. Rather,
the enrollment challenge is simply a smart security
precaution4 along the way to configuring a
new +Intro email account. The one disadvantage of this approach is that it is
not possible to inspect the settings that are ultimately installed until after
the fact.
Configuration profiles are complex beasts. Apple probably needs to do more to help typical end-users understand what it is they’re doing when they install profiles… and, perhaps, to gently discourage them from doing so. That said, profiles (and Apple’s Laissez-faire attitude toward them) are essential to iOS’s continued success in the enterprise. They can’t and won’t simply go away.
(Bogey)men in the middle
It’s worth remembering that not all men-in-the-middle are inherently evil. My app Cloak, an easy-to-use VPN service for OS X and iOS, is effectively one big man-in-the-middle. When you use Cloak, literally every byte you send and receive on the Internet passes through our servers. The benefit is simple: if you’re using a network you don’t trust, like Wi-Fi at a coffee shop or airport, you’re putting yourself at risk. By encrypting your data before it leaves your laptop, Cloak can protect you from a wide range of common attacks, like those made possible by Firesheep. The catch? Once your data reaches our servers, we have to decrypt it and send it onward to its original destination. If we were nefarious (we’re not), we could take a peek along the way. On the whole, I’m convinced that Cloak’s benefits outweigh its costs. But it’s undeniably in-the-middle. It must be weighed and measured as such.
Men-in-the-middle come in all shapes and sizes; it’s no surprise that Cloak and Intro have very different security properties. For example, Intro temporarily strips away the encryption of all email transfer. Cloak, on the other hand, never decrypts independently encrypted data: it can’t! Since email transfer is typically independently encrypted with SSL, Cloak can never see your email. The same goes for your interactions with independently secured websites like, for example, your bank.
As always with complex systems like Intro, the question is whether the rewards eclipse the risks. Even knowing Intro’s risks, I can see how customers — completely sane and thoroughly informed — might still be excited to use it. After all, is Intro truly worse than Gmail itself, which has full access to your email and uses it to serve you ads?
[1] Including confusion in the first version of this post, for which I sincerely apologize. Luckily, my mistake was quickly caught.
[2] Usually. The use of a device enrollment challenge changes this.
[3] In Apple’s parlance, there is no such thing as an MDM profile. Some iOS developers seem to use the phrase to refer to any configuration profile, which isn’t particularly useful. I personally define MDM profile as any configuration profile delivered via OTA Profile Delivery.
[4] Specifically, the use of an enrollment challenge allows LinkedIn to authenticate the recipient, and to encrypt the profile payload.